[comment]: # (mdslides presentation.md --include media) [comment]: # (The list of themes is at https://revealjs.com/themes/) [comment]: # (The list of code themes is at https://highlightjs.org/) [comment]: # (markdown: { smartypants: true }) <style type="text/css"> .reveal { font-size: 2.2em; } .reveal .code-wrapper code { white-space: pre; font-size: 2em; line-height: 1.2em; } </style> <a href="https://github.com/exit-zero-academy/DevOpsTheHardWay.git">DevOpsTheHardWay</a> These are the slides we use in class, you're welcome to explore them. Enjoy your learning journey!
# Elastic Load Balancing and Autoscaling groups  By Alon Itach
### Today's agenda - Load balancer motivation - Listeners and target groups - Application load balancers - Autoscaling groups
### Load Balancers - A load balancer (LB) serves as the **single point of contact for clients**. It accepts incoming traffic from clients and routes requests to its registered **targets**. - Targets may be EC2 instances, IP addresses, and [more...](https://docs.aws.amazon.com/elasticloadbalancing/latest/application/load-balancer-target-groups.html) - LB monitors the health of its registered targets and ensures that it routes traffic only to healthy targets. - LB can map requests across different availability zones in a single region 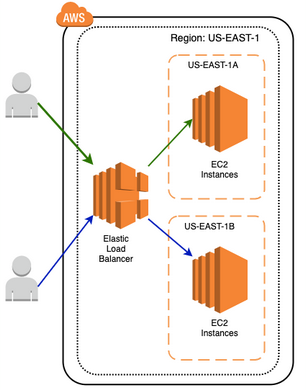
### Listeners and Target Groups - To configure your load balancer, you create **target groups**, and then [register targets](https://docs.aws.amazon.com/elasticloadbalancing/latest/application/target-group-register-targets.html) with your target groups. - You also create **listeners** to check for connection requests from clients, and [listener rules](https://docs.aws.amazon.com/elasticloadbalancing/latest/application/listener-update-rules.html) to route requests from clients to the targets in one or more target groups. - You can use an HTTPS listener to offload the work of TLS encryption and decryption to your load balancer. 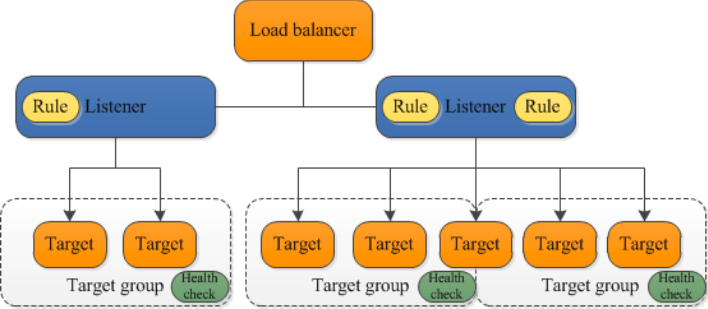
### 3 Types of Load Balancers - [Application load balancer](https://docs.aws.amazon.com/elasticloadbalancing/latest/application/introduction.html) - [Network load balancer](https://docs.aws.amazon.com/elasticloadbalancing/latest/network/introduction.html) - [Gateway load balancer](https://docs.aws.amazon.com/elasticloadbalancing/latest/gateway/introduction.html)
### Application Load Balancer The Application Load Balancer distributes incoming HTTP and HTTPS traffic across multiple targets, as follows: 1. Your client makes a request to your application. 2. The listeners in your load balancer receive requests matching the protocol and port that you configure. 3. The receiving listener evaluates the incoming request against the rules you specify, and if applicable, routes the request to the appropriate target group. 4. Healthy targets in one or more target groups receive traffic based on the load balancing algorithm, and the routing rules you specify in the listener. 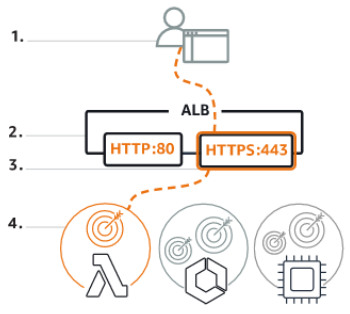
### ALB and HTTP headers HTTP requests and HTTP responses use [header fields](https://docs.aws.amazon.com/elasticloadbalancing/latest/application/x-forwarded-headers.html) to send information about the HTTP messages. HTTP headers are added automatically. - The `X-Forwarded-For` request header helps you identify the IP address of a client when you use an HTTP or HTTPS load balancer. - The `X-Forwarded-Proto` request header helps you identify the protocol (HTTP or HTTPS) that a client used to connect to your load balancer. - The `X-Forwarded-Port` request header helps you identify the destination port that the client used to connect to the load balancer.
### Sticky sessions for the ALB - By default, an ALB routes each request independently to a registered target based on the chosen load-balancing algorithm. - [Sticky session](https://docs.aws.amazon.com/elasticloadbalancing/latest/application/sticky-sessions.html) ensures that all requests from the user during the session are sent to the same target. - This feature is useful for servers that maintain state information in order to provide a continuous experience to clients. To use sticky sessions, the client must support cookies.
### Network Load Balancer Network Load Balancer operated at the Transport layer (TCP, UDP). Good for ultra-high performance, capable of handling millions of requests per second. 1. Clients make requests to your application. 1. The load balancer receives the request either directly or through an endpoint for private connectivity (via AWS PrivateLink). 1. The listeners in your load balancer receive requests of matching protocol and port, and route these requests based on the default action that you specify. You can use a TLS 1. listener to offload the work of encryption and decryption to your load balancer. 1. Healthy targets in one or more target groups receive traffic according to the flow hash algorithm. 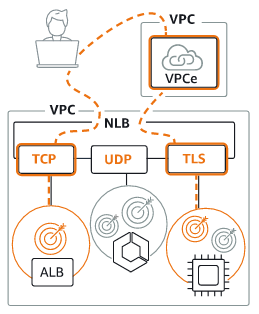
### Gateway Load Balancer A Gateway Load Balancer provides private connectivity between your VPC to a virtual appliances (such as firewalls, intrusion detection and prevention systems, and deep packet inspection systems) in the service provider VPC. 1. Clients make requests to your application. 1. The load balancer receives the request (in the IP layer) based on the route table configured within your VPC, Internet Gateway, or Transit Gateway. 1. The load balancer routes requests to a target group consisting of a 3rd party appliances (for example, firewalls, or URL filtering systems etc.) to process traffic flows. 1. The appliance processes the traffic, and forwards it back to the load balancer, or drops the traffic based on its configuration. 1. The load balancer forwards the traffic to its destination. 
### Gateway Load Balancer - an example [Check Point CloudGuard](https://www.checkpoint.com/products/cloud-native-security/) provides advanced threat prevention, Firewall, IPS, Application Control, IPsec VPN, DLP, Antivirus and Anti-Bot and more security services to customers deploying their application in AWS. Here is how...
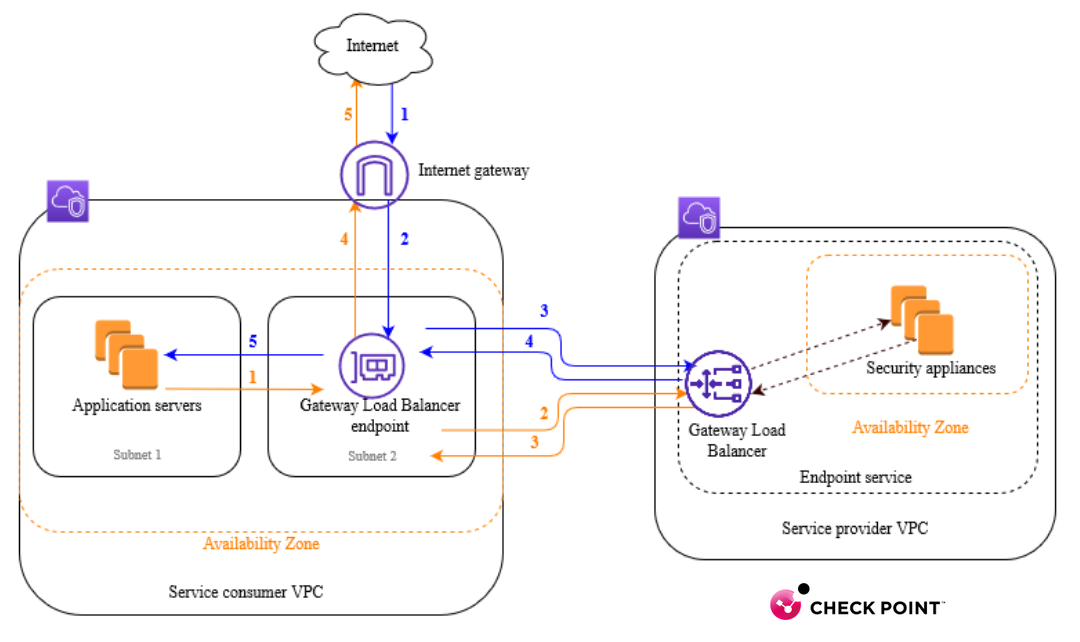 Traffic from the internet to the application (blue arrows): Traffic enters the service your VPC through the internet gateway.
 Traffic is sent to the Gateway Load Balancer endpoint.
 Traffic is sent to the **CheckPoint Gateway Load Balancer**, in their VPC, which distributes the traffic to one of the security appliances.
 Traffic is sent back to the Gateway Load Balancer endpoint after it is inspected by the security appliance.
 Traffic is sent to the application servers (destination subnet).
 Traffic from the application to the internet (orange arrows): Traffic is sent to the Gateway Load Balancer endpoint as a result of the default route configured on the application server subnet.
 Traffic is sent to the Gateway Load Balancer, which distributes the traffic to one of the security appliances.
 Traffic is sent back to the Gateway Load Balancer endpoint after it is inspected by the security appliance.
 Traffic is sent to the internet gateway based on the route table configuration.
 Traffic is routed back to the internet.
### Gateway Load Balancer partners AWS GWLB integrates with a [number of industry-leading partners](https://aws.amazon.com/elasticloadbalancing/partners/), including: - Aviatrix - Check Point - Cisco Systems - cPacket - Glasnostic - Fortinet - HashiCorp - NETSCOUT - Palo Alto Networks - Radware - Trend Micro - Valtix
### Load balancer internals - Before a client sends a request to your LB, it resolves the load balancer's DNS. Amazon DNS servers return one or more IP addresses to the client. These are the IP addresses of the **load balancer nodes** for your load balancer. - The client determines which IP address to use to send requests to the load balancer. The load balancer node that receives the request, selects a healthy registered target and sends the request to the target using its private IP address. 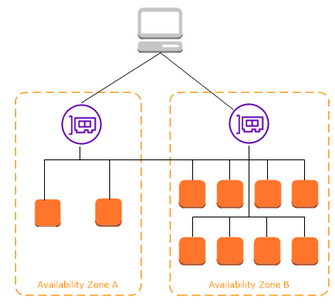
### Load balancer internals - When you create a load balancer, you must choose whether to make it an **internal load balancer** or an **internet-facing load balancer**. - The nodes of an internet-facing load balancer have **public IP addresses**. The DNS of an internet-facing load balancer is publicly resolvable to the public IP addresses of the nodes. - The nodes of an internal load balancer have only private IP addresses. The DNS of an internal load balancer is **publicly resolvable** to the private IP addresses of the nodes. - Both internet-facing and internal load balancers route requests to your targets using **private IP addresses**.
### Load balancer internals - Cross-zone load balancing - When [cross-zone load balancing](https://docs.aws.amazon.com/elasticloadbalancing/latest/userguide/how-elastic-load-balancing-works.html#cross-zone-load-balancing) is enabled (by default in ALB), each load balancer node distributes traffic across the registered targets in all enabled Availability Zones. - When cross-zone load balancing is disabled (can be done only in NLB), each load balancer node distributes traffic only across the registered targets in its Availability Zone. 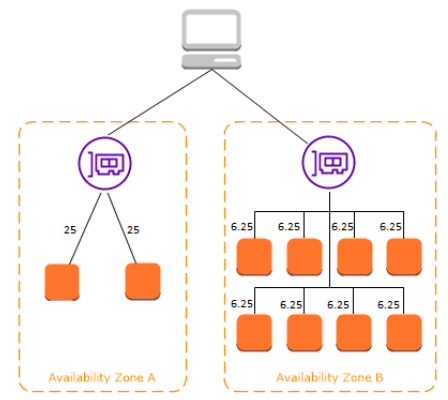
### Amazon EC2 Auto Scaling - [EC2 Auto Scaling](https://docs.aws.amazon.com/autoscaling/ec2/userguide/what-is-amazon-ec2-auto-scaling.html) helps you ensure that you have the correct number of Amazon EC2 instances available to handle the load for your application. - EC2 instances are organized into a [scaling groups](https://docs.aws.amazon.com/autoscaling/ec2/userguide/auto-scaling-groups.html). An Auto Scaling group contains a collection of EC2 instances that are treated as a logical grouping for the purposes of automatic scaling and management. - [Launch template](https://docs.aws.amazon.com/autoscaling/ec2/userguide/launch-templates.html) specifies instance configuration information. It includes the ID of the Amazon Machine Image (AMI), the instance type, a key pair, security groups, and other parameters used to launch EC2 instances. - [Scaling policies](https://docs.aws.amazon.com/autoscaling/ec2/userguide/scale-your-group.html) control how to automatically increase/decrease the size of the group based on a specified increase in demand - No additional fees with Amazon EC2 Auto Scaling 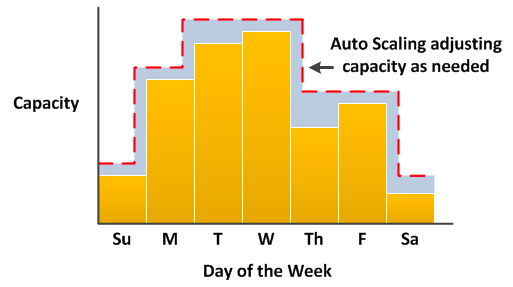
### Distribute instances across Availability Zones - Auto Scaling attempts to distribute instances evenly between the Availability Zones that are enabled for your Auto Scaling group. - Availability Zone auto-rebalancing is supported for certain activities in your scaling group. - When rebalancing, new instances are launched before terminating the old ones.
### Auto Scaling instance lifecycle The following illustration shows the transitions between instance states in the EC2 [Auto Scaling lifecycle](https://docs.aws.amazon.com/autoscaling/ec2/userguide/ec2-auto-scaling-lifecycle.html). 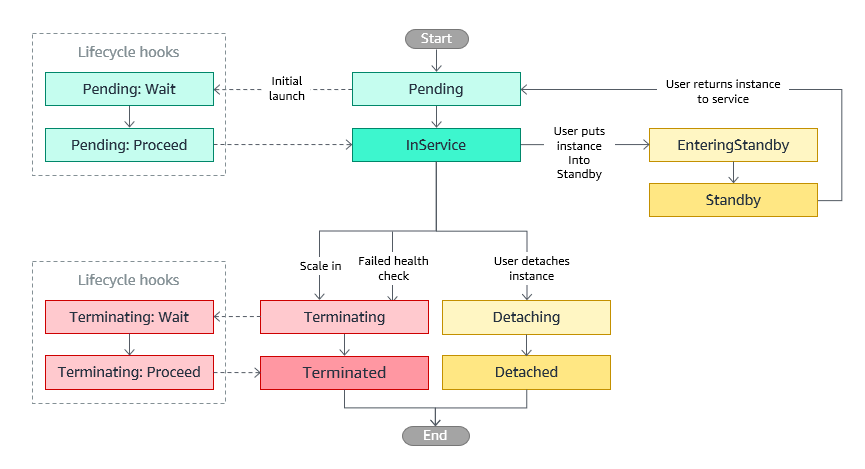
### Auto Scaling instance lifecycle - The following **scale-out** and **scale-in** events direct the Auto Scaling group to launch/terminate EC2 instances and attach/detach them to the group: - You [manually change the size of the group](https://docs.aws.amazon.com/autoscaling/ec2/userguide/as-manual-scaling.html). - You create a [scaling policy](https://docs.aws.amazon.com/autoscaling/ec2/userguide/as-scale-based-on-demand.html) to automatically increase/decrease the size of the group based on a specified change in demand. - You set up [scaling by schedule](https://docs.aws.amazon.com/autoscaling/ec2/userguide/ec2-auto-scaling-scheduled-scaling.html). - The lifecycle starts when the Auto Scaling group launches an instance and puts it into service. - The lifecycle ends when you terminate the instance, or the Auto Scaling group takes the instance out of service and terminates it.
### Auto Scaling and Load Balancer Integration The following summarizes the workflow for registering/deregistering an instance with a load balancer for a scale-out and scale-in events. 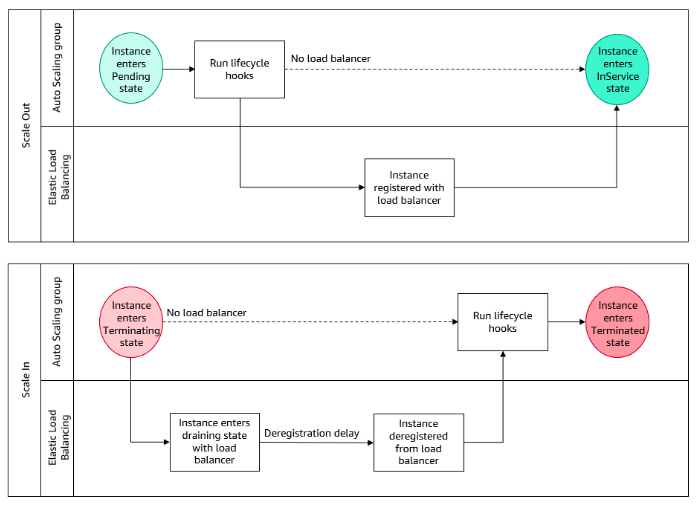
### Example: Auto Scalable Web App Architecture 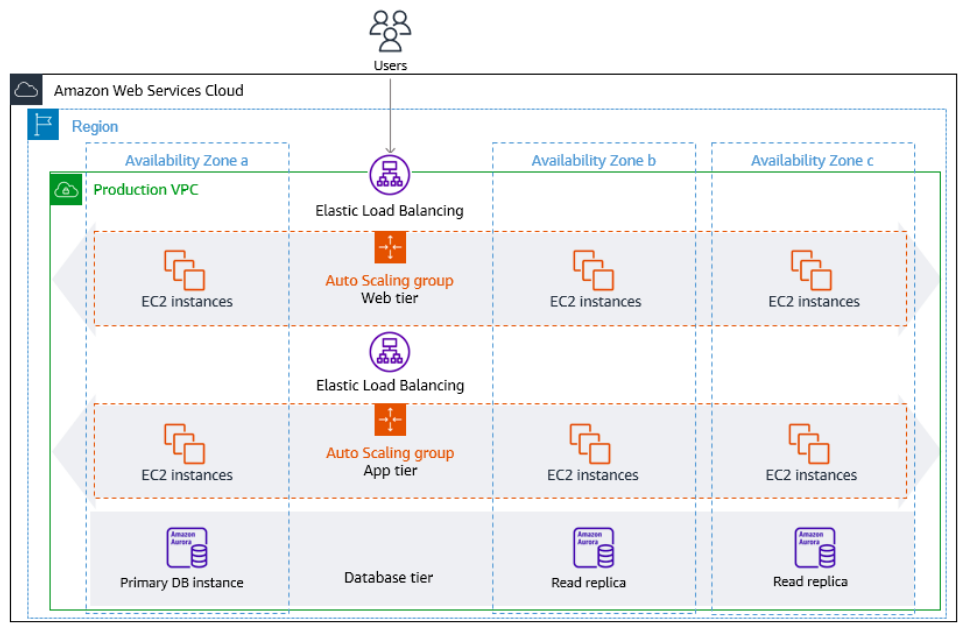
# Thanks